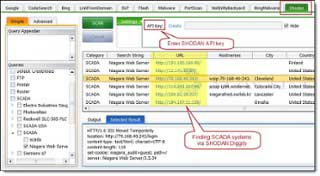
Reasonable Threat Intelligence
Managed Service Providers Under Attack In the past month, a Managed Service Provider (MSP), or what many registered investment advisers might utilize as their outsourced IT Provider, was breached, exposing up to 2000 user endpoints to issues of disruption and perhaps worse. The IT Vendor was subsequently urged to pay ransom of [...]